The Internet of Things (IoT) refers to the interconnectivity of everyday devices, such as home appliances, wearable devices, and vehicles. These devices, equipped with sensors and internet connectivity, are designed to collect and exchange data to enhance user experience and efficiency. However, as the number of IoT devices increases, so does the risk of privacy breaches and cyber attacks. Therefore, it is crucial to implement effective privacy measures to safeguard IoT devices and user data.
Effective privacy measures for IoT devices include securing the device, network, and data. This can be achieved through the use of strong passwords, encryption, and two-factor authentication. Additionally, it is essential to update the software and firmware of IoT devices regularly to patch security vulnerabilities. Furthermore, users should be aware of the data collected by IoT devices and the parties with access to this data. They should also have the option to control the data collected and shared by these devices.
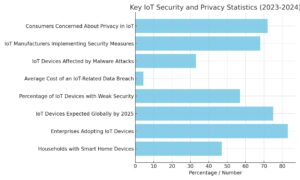
| Statistic | Percentage / Number | Source/Year |
|---|---|---|
| Households with Smart Home Devices | 47% | Statista, 2024 |
| Enterprises adopting IoT devices | 83% | Gartner, 2023 |
| IoT devices expected globally by 2025 | 75 billion | IDC, 2023 |
| Percentage of IoT devices with weak security | 57% | IoT Security Foundation, 2023 |
| Average cost of an IoT-related data breach | $4.4 million | Ponemon Institute, 2024 |
| IoT devices affected by malware attacks | 33% | Microsoft Security, 2023 |
| IoT manufacturers implementing security measures | 68% | PwC, 2023 |
| Consumers concerned about privacy in IoT | 72% | Consumer Reports, 2024 |
Understanding IoT and Privacy

The Internet of Things (IoT) is a network of interconnected physical devices, vehicles, and other items that use sensors, software, and other technologies to collect and exchange data with other devices and systems over the internet.
IoT devices are becoming increasingly popular in homes, businesses, and industrial settings, and they offer a wide range of benefits, including improved convenience, efficiency, and productivity.
The IoT Ecosystem
IoT devices are a key component of the IoT ecosystem. They include a wide range of devices, such as smart thermostats, security cameras, wearable fitness trackers, and industrial sensors.
These devices are designed to collect and transmit data to other devices and systems, and they often rely on cloud-based services to store and process data.
Privacy Concerns in IoT
Privacy is a major concern in the IoT ecosystem, as IoT devices can collect a wide range of personal and sensitive information about users. For example, a smart home security camera can capture video footage of a user’s home, while a wearable fitness tracker can collect data about a user’s health and fitness habits.
This information can be used by hackers or other malicious actors to steal identities, commit fraud, or engage in other types of cybercrime. To address these privacy threats, effective privacy measures for IoT devices are essential. These measures can include encryption, authentication, access controls, and other security technologies that are designed to protect user privacy.
Additionally, IoT devices should be designed with privacy in mind, and they should include clear privacy policies that outline how user data is collected, used, and shared.
Securing IoT Devices
When it comes to securing IoT devices, there are several measures that can be taken to ensure maximum protection against potential threats.
Authentication and Access Control
One of the most important security measures for IoT devices is authentication and access control. This involves ensuring that only authorized users have access to the device and its data. To achieve this, multi-factor authentication can be used, which requires users to provide multiple forms of identification before they can access the device. Additionally, strong passwords, patterns, and PINs should be used to prevent unauthorized access.
Encryption and Data Protection
Another important aspect of securing IoT devices is encryption and data protection. This involves encrypting all data transmitted between the device and the network, as well as encrypting all stored data on the device. This can prevent hackers from intercepting and stealing sensitive information. Additionally, data backups should be performed regularly to ensure that data can be restored in the event of a security breach.
Network Security Measures
Network security measures are also crucial for securing IoT devices. This involves implementing a firewall to prevent unauthorized access to the network, as well as using security protocols such as WPA2 to encrypt all data transmitted over the network. Additionally, all network-connected devices should be updated regularly to ensure that they have the latest security patches.
Best Practices for IoT Privacy
When it comes to IoT devices, privacy is a major concern. Here are some best practices to follow to protect your personal data and privacy.
Device and Network Management
One of the most important things you can do to protect your IoT devices is to properly manage them. This includes changing default passwords, keeping software and firmware up to date, and implementing strong passwords. Default passwords are often easy to guess, making it easy for hackers to gain access to your devices. By changing them to something stronger, you can make it much more difficult for unauthorized individuals to access your devices. Another important aspect of device and network management is keeping your software and firmware up to date.
Manufacturers often release security patches and updates to address vulnerabilities and improve security. By regularly updating your devices, you can ensure that you have the latest security features and protections.
Regulatory Compliance and Standards
Regulatory compliance and standards are also important for protecting your IoT devices. Many countries have laws and regulations that govern the use of IoT devices and the protection of personal data. By complying with these regulations, you can ensure that your devices are secure and that your personal data is protected. In addition to regulatory compliance, there are also industry standards that can help ensure the security and privacy of your IoT devices. For example, the Open Web Application Security Project (OWASP) has developed a set of guidelines for securing IoT devices. By following these guidelines, you can ensure that your devices are as secure as possible.
Emerging Technologies and Future Trends
As IoT devices become more ubiquitous, there is a growing need for enhanced security measures to protect sensitive data and personal information.
Artificial Intelligence and IoT

Artificial intelligence (AI) is being used to enhance IoT security by analyzing large datasets and identifying patterns that could indicate cyberattacks. AI can also be used to detect anomalies in device behavior and trigger alerts when suspicious activity is detected. In addition, AI can be used to automate security measures, such as updating firmware and patching vulnerabilities.
Blockchain for Enhanced Security
Blockchain technology is being explored as a way to enhance security for IoT devices. By using a decentralized ledger, blockchain can provide a tamper-proof record of device activity, making it more difficult for cybercriminals to launch attacks. Blockchain can also be used to create secure, peer-to-peer networks between IoT devices, reducing the need for centralized servers that can be targeted by hackers.
Frequently Asked Questions
How can users enhance the privacy of their IoT devices?
Users can enhance the privacy of their IoT devices by following some best practices, such as changing default passwords, disabling unnecessary features, and keeping firmware and software updated. Additionally, users should be cautious about the data they share with IoT devices and only provide necessary information.
What are the most critical security concerns for IoT devices?
The most critical security concerns for IoT devices include weak authentication and authorization protocols, insufficient encryption, lack of secure communication channels, and unpatched vulnerabilities. These issues can lead to unauthorized access, data breaches, and even physical harm.
Why is it essential to prioritize security in IoT ecosystems?
Prioritizing security in IoT ecosystems is essential because IoT devices are often connected to critical infrastructure, such as power grids, transportation systems, and healthcare facilities. A security breach in these systems can have severe consequences, including financial loss, reputational damage, and even loss of life.
What steps should be taken to mitigate vulnerabilities in IoT networks?
To mitigate vulnerabilities in IoT networks, manufacturers should follow security-by-design principles, conduct regular security audits, and provide timely firmware and software updates. Users should also be informed about the risks and take necessary precautions, such as using strong passwords and avoiding unsecured networks.
How do privacy concerns in IoT impact user trust and adoption?
Privacy concerns in IoT can impact user trust and adoption. Users may be hesitant to adopt IoT devices if they perceive them as a threat to their privacy. Therefore, it is crucial to address privacy concerns proactively and transparently to build trust with users.
What strategies are recommended for securing IoT devices against cyber threats?
Several strategies are recommended for securing IoT devices against cyber threats. These include implementing strong authentication and encryption protocols, using secure communication channels, and regularly updating firmware and software. Additionally, manufacturers should conduct regular security audits and provide user education and awareness programs.